Discovery integration
Understanding ServiceNow's Discovery and Configuration Management Database (CMDB) capabilities in IT Operation Management (ITOM)
On this page
Introduction
ServiceNow has a product called Discovery in the IT Operation Management (ITOM) to collect Configuration Items (CIs) with all the information we can get from the infrastructure. This is crucial for organizations to maintain an accurate and efficient IT environment. All the CIs are stored in the Configuration Management Database (CMDB). Discovery is running from the Management, Instrumentation, and Discovery Server (MID Server) in the customer domain.
Agentless
ServiceNow’s ITOM Discovery is a powerful tool that discovers the entire IT infrastructure, creating an accurate and up-to-date record in ServiceNow CMDB. Agentless means that it does not require any permanent software to be installed on any computer or device to be discovered, providing a non-intrusive and efficient approach compared to agent-based discovery.
Discovery of physical and logical components
It discovers both physical and logical components, including virtual machines, servers, storage, databases, applications, and more, providing a comprehensive view of the IT infrastructure that aids in better resource management and planning.
Application Dependency Mapping (ADM)
It provides ADM, identifying upstream and downstream dependencies to the TCP port and process level. This detailed mapping is essential for risk management, impact analysis, and efficient troubleshooting.
Data Model
The ServiceNow CMDB is built on a single data model with a standard taxonomy, predefined semantics, consistent format, data quality standards, and common processes. This unified approach simplifies data management and enhances data accuracy and usability.
Cloud environment support
Discovery provides real-time visibility of public and private cloud environments by integrating with notification-driven cloud vendor configuration interfaces such as Microsoft Azure and the Amazon AWS Config API. It supports multiple cloud platforms including Amazon AWS, Microsoft Azure, Google GCP, IBM Cloud, and Oracle Cloud, facilitating seamless hybrid and multi-cloud management.
Identification and Reconciliation Engine (IRE)
IRE is an underlying key component in Identification and Reconciliation, providing a centralized framework to perform identification and reconciliation processes across different data sources. IRE uses identification rules, reconciliation rules, and IRE data source rules when processing incoming data before inserting that data into the CMDB. An example of IRE in action is its ability to accurately identify and reconcile data from diverse sources, ensuring data consistency in the CMDB.
Agent-based
To be described
Software
Agent-based discovery is a type of software used to discover assets and services in a network using agents, and autonomous programs that run on the devices being discovered.
Collecting information
These agents are responsible for collecting and transmitting information to the centralized management system, making it ideal for scenarios requiring deep and continuous monitoring. Agent-based discovery systems use agents on individual devices that make periodic callbacks to a CMDB.
Architecture
To be described
MID Server
A MID Server, which constantly queries the instance for probes to run, executes the instructions in the probe or in the pattern that the probe specifies. The MID Server then returns the results to the instance, where sensors process them. The MID Server does not retain any discovery information. It is a Java application installed on a dedicated server in the customer domain, designed with security in mind to protect sensitive discovery data.
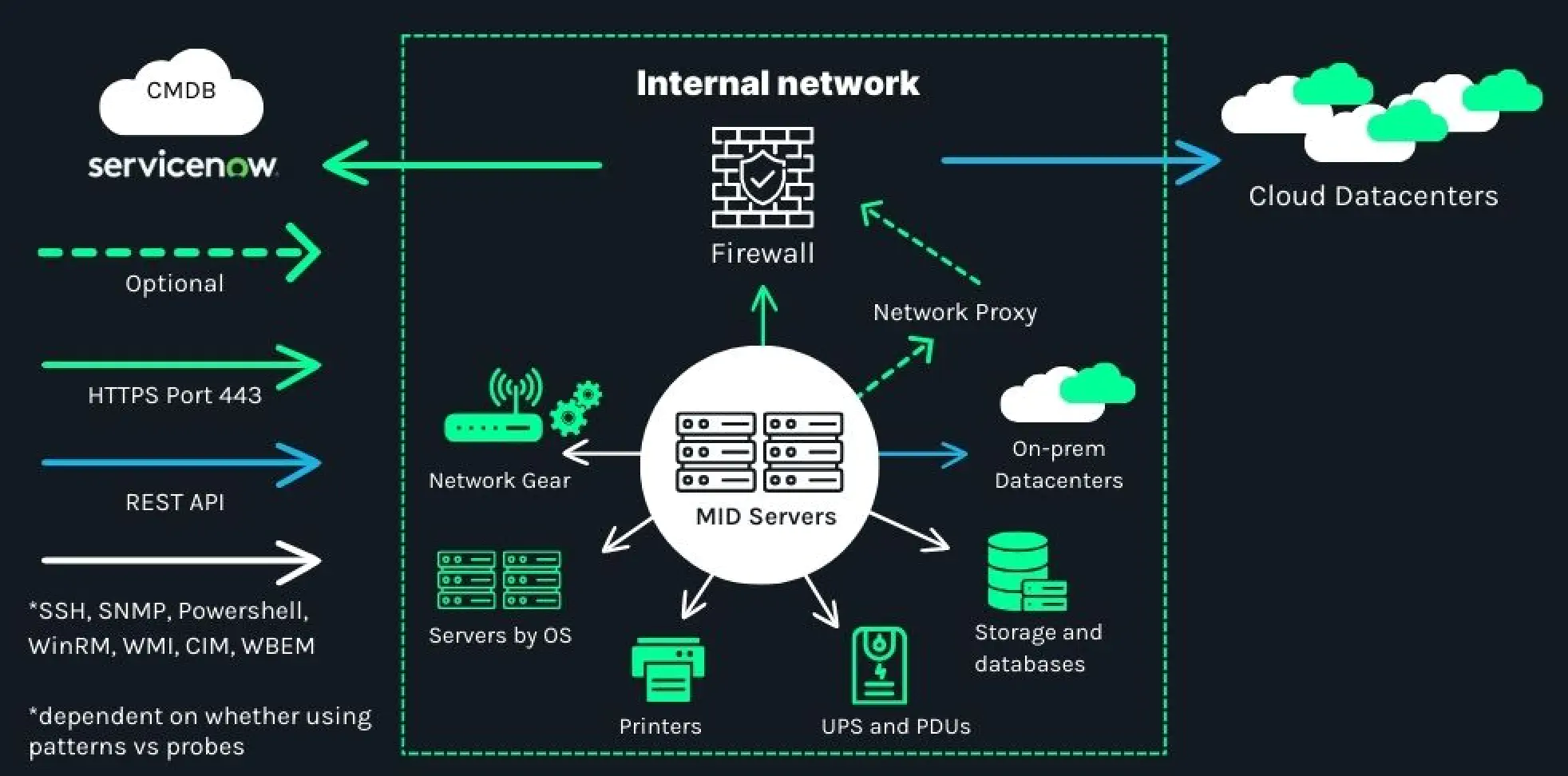
Firewall and network requirements
For a MID server to work, we need to ensure the firewall requirements are in place before we start configuring and running discovery. We have a few mandatory sets of rules, while there is an additional ruleset available for running discovery of special services like storage, network, etc. Adequate configuration of these rules is critical for successful and secure discovery operations.
Certificate requirements for MID Server
ServiceNow MID servers are in charge of gathering inventory of all assets available for ServiceNow. Normally the discovery would use the domain certificate or the public certificate provided by the client/appliance/server. Some discovery protocols also allow you to run unencrypted discovery, where valid certificates are not needed. However, for most, this is mandatory, aligning with compliance and security standards.
Credentials
To get the information inside the servers, Discovery needs credentials for login. All credentials are stored in a protected database called Secret Server. The MID Server will get the credentials from Secret Server every time we run discovery. The credentials we use for running discovery are local admin. The integration with Secret Server not only ensures security but also aids in compliance with data protection regulations.
Other data source
To get a fulfilled CMDB we, in some cases, need to use other sources for collecting data as System Center, Cisco, and more. Integrating these multiple sources enriches the CMDB, providing a more comprehensive view of the IT infrastructure.
Stored data for ServiceNow
All data from discovery will be stored in ServiceNow. This data is stored in Europe, Amsterdam, and Dublin, adhering to regional data storage regulations and ensuring compliance with data protection laws.